Windows
Architecture
Analyzing
Requirements and Defining Solution
Architectures
1. BUSINESS REQUIREMENTS
ANALYSIS
PROJECT
SCOPE
(Analysing Requirements)

Define Project Responsibilities then
-
Divide
Responsibilities into individual tasks
-
Determine how many
Geographical Areas will be involved
-
Get estimate of number
of people who will be using your application
-
Understand how quickly
client wants the application implemented
ANALYZE THE EXTENT OF
BUSINESS REQUIREMENTS
(Design dealing with client's
line of business)
|
Establish Business Requirements
(Rules)
|
-
Description of a
specific task in client's business work flow. e.g.,
inventory control, inventory falling below a
certain amount, re-order stock.
|
|
Establish Type of Problem
|
|
|
Establish Customer Quality
Requirements
|
|
|
Cost-Effectiveness
|
|
ANALYZE CURRENT
PLATFORM AND INFRASTRUCTURE
-
Analyze the technology
already in use
-
Consider input from
staff (part of infrastructure) and should be part of
solution
ANALYZE THE IMPACT OF
TECHNOLOGY MIGRATION
-
Schedule time required
for migration process
-
Test the effects of
migration
-
Minimize business
interrupts during Migration
-
Familiarize personnel
with new changes
-
Prepare contingency
plans for unexpected failure
-
Establish an
Application environment
-
Infrastructure
Company's every part that is not a computer, cables,
etc.
-
Hardware and
software constraints and requirements to run
Applications
-
Identify
Organisational Constraints
-
Identify your
audience
-
Establish an
Implementation Schedule
ANALYZE SECURITY
REQUIREMENTS
-
Consider
-
Which groups
requires access
-
Which data should
each group be given access to
-
What kind of access
should each group be given
-
Identify roles of
Administrators, Groups, Guests and Clients
-
Establish level of
Fault Tolerance / Security Context
-
Identify Impact of
Security
-
Plan for
Maintainability
-
Plan distribution of a
security Database
-
Plan for Auditing /
Logging
-
Identify required
level of security needed
-
Analyze existing
Security Policies
ANALYZE PERFORMANCE
REQUIREMENTS
-
Consider
-
Interoperability
with existing standards
-
Response Time
expectations
-
Transactions /
minute
-
Bandwidth
-
Capacity
-
Bottlenecks
-
Peak vs. Average
requirements
ANALYZE
MAINTAINABILITY REQUIREMENTS
-
Consider
-
Deployment
-
Maintenance
-
Redeployment
ANALYZE EXTENSIBILITY
REQUIREMENTS
ANALYZE AVAILABILITY
REQUIREMENTS
-
Consider
-
Hours of
operation
-
Level of
availability
-
Geographic scope
-
Impact of downtime
ANALYZE HUMAN
FACTORS
ANALYZE INTEGRATION
REQUIREMENTS
ANALYZE EXISTING
BUSINESS PRACTICES
-
Consider
-
Current business
practices
-
Customer's needs
-
Budget
-
Implementation and
training
-
Quality control
requirements
-
Process
engineering
-
Legal issues
ANALYZE SCALABILITY
REQUIREMENTS
2. TECHNICAL SOLUTIONS /
ARCHITECTURE
IDENTIFY THE APPROPRIATE SOLUTION TYPE /
TIER
Single-Tier Application Model
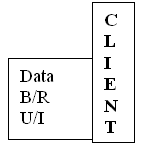
-
-
Two-Tier
Application Model
-
Business rules (B/R)
and user interface (U/I) is on client
-
Client makes
intelligent queries and processes them
-
Database (Data) is
only kept on server for central storage
-
Advantages

-
N-Tier / Multiple
Tier Application Model
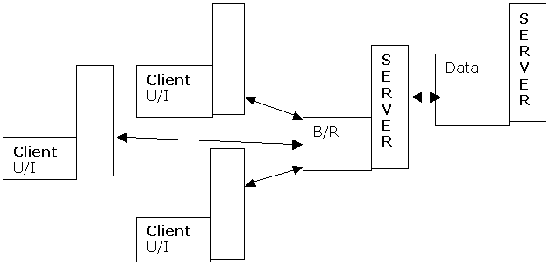
MEETING USE CASE
SCENARIOS
(Which technologies are appropriate for
implementation of a given business solution?)
|
ELECTRONIC DATA INTERCHANGE (EDI)
|
|
|
THE INTERNET
|
|
|
POSIX
(PORTABLE OPERATING SYSTEM INTERFACE FOR
UNIX)
|
|
|
SOLUTIONS IN USE CASE SCENARIOS
|
-
Enterprise
Solutions
-
Distributed
Solutions
-
Centralized
Solutions
-
Collaborative
Solutions
|
CHOOSING DATA STORAGE
ARCHITECTURE
FEASIBILITY
TESTING
CONCEPTUAL AND LOGICAL
DESIGN
DEVELOP AN APPROPRIATE
EDPLOYMENT STRATEGY
-
Break down application
in series of phases/versions
-
Plan test environment
for each test phase
-
After testing plan a
test rollout Dry run of how you will implement
product
-
Execute the test
rollout
-
Deploy this phase to
the production environment
-
Collect and analyze
bug reports
-
Fix Bugs
-
Repeat from second
step (Plan test ...) for next phase of product
3. DEVELOPING DATA MODELS
DBMS (Database Management
System) - Computer Application providing the means and
methods to permit a user to interact efficiently with a data
source
Types of DBMS
Methodologies
Flat-File
-
e.g. Telephone
directory
-
Data is stored in one
large file
-
Relies on standard
file I/O processes
-
Contains only one
record structure
-
Uses no links between
separate records
-
Relatively fast
-
Can become very big
and hold redundant data
-
Hierarchical
Database
-
Single flat file is
replaced with series of tables linked in a structured
relationship
-
Child record can be
linked to only one parent
-
Link between a child
and parent record is permanent
-
Child records can only
be reached through a parent record

-
Relational
Database
-
Stores data in one or
more tables which can be linked to any other table
-
Consists of Entities
(Tables), Fields (Columns) and Records (Rows)

Types of DBMS
Methodologies
-
Analysing the
relational data structure of a database use ERA
-
ERA assists in
defining three things about data:
-
The entities
described
-
Kernel entity
describe only one entity, not used to define
relationships
-
Associative
entity ties kernel entities together
-
Characteristic
entity provides additional information about a
specific kernel/associative entity
-
The attributes of
the entities
-
Relationship between
the entities
-
Linking one table
with another for queries
-
Makes use of two keys
-
Primary Key
Unique value for each record in the entity,
referenced by,
-
Foreign Key -
Corresponds to PK of another entity
-
One-To-One
Relationship
-
One-To-Many
Relationship
-
Many-To-Many
Relationship
-
Joining entities -
five types
-
Inner Join -
Relates two tables together and returns all records from each table that have a matching
record in another table
-
Left Outer Join
- All records in the left table are returned, but
only matching records from the right table are displayed.
-
Right Outer Join
- Opposite to Left Outer
-
Full Outer Join
- Returns all matching records from both tables, but nulls are placed where other records are
retrieved, but do not match
-
Cross Join - Two
tables are related but a set of fields to relate to is not provided. All possible combinations of
all rows in the table is made = Cartesian
Product
APPLYING
NORMALIZATION
(Process of removing redundancies from
stored data)
|
Advantages
|
|
|
Rules
of Normalization = Normal Forms:
|
-
First Normal
Form
-
No repeating
groups. Data in rows and columns must
contain
only one value
Every record
in the table must be unique and no duplicates are permitted
-
PK must
satisfy several conditions
-
All data must
be non decomposable the data can not be
broken down into simpler pieces
-
Second Normal
Form
-
Third Normal
Form
|
|
Denormalization
|
-
Restore
attributes
-
Restore
duplicate keys
|
APPLYING DATA
INTEGRITY
(Refers to the accuracy and consistency of
the data contained in a database)
|
Entity integrity
|
|
|
Referential integrity
|
-
Guarantees the
logical consistency of the database by ensuring the
values for PK and FK pointing to PK are always
in agreement
-
Three rules that
can be imposed when updating PK:
-
Restrict
Delete / Update on PK not allowed
-
Cascade Any
change to PK is automatically applied to all
FK
-
Nullify
Before update is done to PK all corresponding FK
values are set to null
-
CONSIDER
BUSINESS RULES AND CONSTRAINTS
|
4. PRINCIPLES OF USER INTERFACE
DESIGN
WHAT MAKES A GOOD
DESIGN?
|
User
Control
|
The
user must be able to control everything about the
application.
|
|
Directness
|
The
user must see direct results that they take in your
application.
|
|
Consistency
|
The
Environment must be consistent eg: Windows 95/98
environment.
|
|
Forgiveness
|
Tell
users before they make mistakes; e.g., Min/Close
button in Windows, difference in closing and
minimising.
|
|
Feedback
|
Application must communicate with users, when
busy, etc.
|
|
Aesthetics
|
Interface must be visually
appealing.
|
|
Simplicity
|
Only
show user what he needs, hide more complex concepts
until asked
for = progressive
disclosure.
|
|
Accelerator keys
|
Use of
shortcut keys, eg: Alt & Ctrl A
keys.
|
|
Choose
the correct controls
|
-
TabStrips
-
Tool, Progress
& StatusBars
-
Tree and
ListViews
-
Sliders, text
boxes, labels, etc.
|
|
Using
MDI's / SDI's
|
|
|
Adding
Shell extensions
|
-
File Object
Any item within the shell, e.g. Printers
-
File Class
Owner of particular type of object e.g. MS Excel
file is a file class
-
Handler Code
that implements a specific shell extension
-
Some shell
extension types include:
-
Context Menu
Editor Context menu appears when user clicks
on a file object with the secondary mouse
button
-
Icon Handler
Adds icons to the classes for a specific file
object
-
Property
Sheet Handler Adds property sheet specific to
a file class or file object
-
Will you use
Console Applications?
-
Accessibility
Visual/hearing impaired or spelling impaired
consideration for users
-
Deployment
Platform Consider
-
32 Bit
Windows or 16 Bit Windows
-
Internet or
Intranet, Browser compatibility, etc. must be
kept in mind
-
User
assistance:
-
Fully indexed
and searchable help topics
-
Context-sensitive help pressing F1
-
"What's this"
Help, ToolTips, Status Bars
|
5. DERIVING THE LOGICAL &
PHYSICAL DESIGN
-
Logical design =
Theory and planning behind the design and implementation
(Physical Design)
-
Logical design is
concerned with behaviour from an abstract perspective
-
Physical Design is
concerned with the actual implementation of the design
-
Logical design is
independent of technology constraints
-
Physical design must
consider system hardware and software where the interface
will be employed
DERIVING THE
LOGICAL/CONCEPTUAL DESIGN
-
Requires that you
begin with a structured base and evolve a solution that
will provide a physical implementation satisfying
business requirements
-
Make use of the
following models to structure your design
|
1. Context
Model |
-
The process that
surrounds your application
-
Consider
external interactions, draw a diagram of the
interaction between your application and other
business processes |
|
2. Work-Flow
Model |
|
|
3.
Task-Sequence Model
|
-
Describes
internal flow of operation inside the
application
-
Reference the
previous two models to generate this model
-
The
task-sequence model describes what your application
needs to do to generate the proper inputs and
outputs in a proper sequence
-
Tasks in this
model differs from the ones in the work-flow model
in that these tasks are internal to your
application, while the tasks in the work-flow model
are external
-
Focus on what
the application does, rather than on what the users
need it to do
-
Draw a flow
chart to outline the process
-
Actions(Rectangular boxes) to be
performed
-
Decision
points(Diamonds), contains a question with all
possible answers
-
Connections(Arrows between action and
decision points), direction of arrow shows
sequence of the elements
|

|
1.
Identifying business objects and services
|
|
|
2.
Interface design
|
|
|
3.
Business object interdependencies
|
|
|
4.
Employing usage scenarios to validate logical
design
|
|
|
5.
Design Revisions
|
-
Producing a
complete logical design does not happen in one
step
-
Begin by
creating an initial design, then criticise and
dissect it, refining the design and adding detail
|
-
Logical Design Risk
Factors to Consider
-
Behaviour of the
logical design does not match usage scenarios
-
Logical design must
be co-ordinated with the enterprise architecture (Hardware/software)
-
Must not depend on
external systems
-
Baselining the Logical
Design
-
Asses the potential
impact of the logical design by considering
-
Performance
-
Maintainability
-
Extensibility
-
Scalability
-
Availability
-
Security
DERIVING THE PHYSICAL
DESIGN
-
Means translating the
logical design into a cost effective solution
-
Roles filled by teams
in a physical design
-
Product Management
Governs the physical design process
-
Development
Creates the design
-
QA/Testing Plans
test process
-
Logistics Plans
appropriate distribution
-
User Education
Plans training programs
-
Assessing the impact
of the design, consider
-
Performance
-
Maintainability -
considering:
-
Good three tier
design
-
Designing for
change
-
Business rules
-
Code
readability
-
Extensibility How
new functionality can be added to the system with minimum cost and time impact
-
Scalability e.g.,
Must perform the same if 10 or 1000 users makes use of
the system. Consider
-
Component state
-
Just in time
activation
-
Clustering
-
Resource
pooling
-
Availability How
often the system is able to perform, measured by MTBF (mean time between failure) and MTTR (mean time
to recovery); consider
-
Security
-
Physical design as a
process: The process of
turning a logical design into a physical solution and
involves a sequence of events
-
Allocating services
to components
-
Distributing
components across the network
-
Refine component
packaging and distribution
-
Define component
interfaces as a mechanism for implementing the service relationship between components
-
Determine physical
media storage, how data will be accessed and distribution of physical data
-
Validate the design
to ensure the physical design is consistent with the logical design and overall enterprise design
6. THE SOLUTIONS FRAMEWORK
Composed of seven
models
|
1.
Team Model
|
-
For building
high performance teams that deliver
-
Team must know
who does what
-
Must know who is
in charge |
|
2. Process Model
|
-
Judging
development trade-offs
-
Addresses
explicit accountability for teams
-
Addresses
project risks early in the planning stages
-
Defines critical
milestones for tracking development
-
Characteristics
-
Envisioning
Vision statement provides product/service
goals
-
Planning
Defines customer expectations
-
Developing
Establish series of interim milestones, debugging,
testing, etc.
-
Stabilisation
Rigid operational requirements for thorough
testing
|
|
3.
Development /Application Model
|
|
|
4.
Solutions Design Model
|
|
|
5.
Enterprise Architecture Model
|
|
|
6. Infrastructure Model
|
|
|
7.
Total Cost of Ownership Model
|
|
7. DEPLOYMENT ISSUES
-
Method of distributing
your application
-
Deployment
Medium
-
Floppy Disks
Deployment (1.2 / 1.44/ 2.88MB capacity)
-
CD-ROM Deployment
(650MB capacity)
-
Network Deployment -
Consider speed, bandwidth and reliability
-
Internet Deployment
Webserver fulfils task of files server, user connects
to server and downloads files
-
Deployment
Methods
8. COM (COMPONENT OBJECT
MODEL)
ADVANTAGES IN THE
COM
-
More productive in
using and reusing software
-
Offers opportunity
to develop for niche applications, e.g., Add-on
components to existing applications
-
For vendors,
distributed operating systems can be tailored to user's
needs
-
End users have a
wide variety of choices
-
Corporate
standpoint, component software can reduce costs for
in-house development
-
MS OLE standard was
first step in the creation of component software
COM COMPONENT SOFTWARE
ARCHITECTURE
-
All services
supplied to users by COM, share a common requirement
-
COM supplies
supporting mechanisms for
-
Robust evolution
of component-based applications and systems
-
Communications
between components, between processes and across
network boundaries
-
Dynamic loading of
components
-
Error and status
reporting
-
Shared memory
management between components
-
Component Software
Problem
BENEFITS OF COM
INTERFACES
-
Increased process
speed and minimal overhead
-
Reusable
interfaces
-
Local/remote
transparency allowing object to be local or
networked
-
Language
independence
-
Virtual function
tables (vtables in memory) = COM can be adapted to a
variety of platforms by defining the vtables = any
language that supports function calls via pointers,
e.g., C/C++, Pascal(Delphi) Small Talk, Basic and Ada
can be used to write components
COMPONENT OBJECT
INTERFACES
COMPONENT OBJECT
LIBRARY
-
Part of
Windows system, providing basic mechanisms to support COM,
it provides
-
Connections between
components
-
Mechanisms to make
IUnknown calls across processes
-
Underlying
mechanisms for launching
components
COMPONENT OBJECT
SERVERS
-
Is a body of
code implementing a component object's services (methods and
functions)
-
Uses server
code to create component object instances and in turn the
object instance provides the services to the component
object client
9. OBJECT LINKING AND
EMBEDDING
-
Mechanism to
allow users to create compound documents
-
Object = any
set of data from one application treated as a unit
-
Compound
documents = documents that can contain objects created and maintained by multiple applications
-
Embedding =
just like pasting, gives the client a complete and
independent copy of the data, but an object remembers
its origin and can be edited
-
When a
document contains all the data for an object the object is
embedded
-
When a
document contains only a reference pointing to data in
another document the object is linked
-
OLE is
composed of a group of interrelated concepts, they are:
|
Linking and embedding
|
|
|
In-Place activation
|
|
|
Automation
|
-
Mechanism to
allow one application to drive another
-
Driving
application = automation client / automation
controller
-
Driven
application = automation server / automation
component |
|
Compound File
|
|
|
Uniform Data Transfer (UDT)
|
|
|
Drag and Drop
|
|
|
Component Object Model (COM)
|
|
OLE STRUCTURED
STORAGE
OLE Structured Storage is
an OLE supported technology for storing and maintaining files
composed of
two or more OLE elements from different
sources in a single document file and involves three elements
|
1. Compound File
|
-
OLE supported
structured storage implementations and supports
IStorage, IStream and ILockBytes interfaces
-
Is any document
containing linked and/or embedded objects in
addition to the document's native data
-
Advantages
-
Incremental
File Access Individual object within the
compound file can be accessed without loading the
entire file
-
File Access
Modes
-
Transacted
Keeps both old and new copies of a document
until instructed to save or undo the changes
-
Direct
Makes immediate changes to the document, without
ability to later undo the changes
-
Disadvantages
-
Size and
performance
-
Fragmentation
|
|
2. Storage Object
|
|
|
3.
Stream Object
|
|
10. ACTIVEX CONTROLS
Comprises a group of
technologies to allow developers to create Internet applications using familiar tools and technologies.
|
Parts
of the ActiveX family
|
-
Active
Scripts
-
ActiveX
Controls
-
ActiveX
Documents
-
ActiveX Server
framework
-
Code download
and verification
-
HTML
Extensions
-
Internet ActiveX
Controls
-
Internet data
download services
|
|
Foundation of creating ActiveX controls consist
of eight elements
|
-
COM Every
ActiveX control is a COM object exposing the
IUnknown interface
-
Compound
Documents Any document that includes linked or
embedded objects and it's own native data
-
Connectable
Objects Allows the control to communicate with a
client object by making use of incoming and outgoing
interfaces
-
OLE Automation
Permit access to the control's interface through the
client supplied programming language to users
-
Persistence
storage ActiveX controls can implement different
persistence interfaces to save a control's state
-
Property Pages
Displays internal properties of an control in a
tabbed dialog box
-
Uniform data
transfer Model for exchanging data through the
clipboard, drag-and-drop or automation
-
System-provided
font and image objects ActiveX controls can use
system - supplied fonts and pictures to enhance
visual appearance
|
11. GENERAL APPLICATION
ARCHITECTURE
Services design model
defines three services
|
1.
User Services deals with interaction between the user
and the application and consists out of the following
tasks
|
-
Receiving data
input from users
-
Packaging user
input for further use
-
Data
formatting
-
Reporting
-
Managing user
preferences
|
|
2. Data Services interact with actual data source.
Its four functional areas are
|
|
|
3. Business Services is the physical process of
getting the client to talk to the server and may
include any of the following tasks
|
|
Practice making use of
Microsoft Transaction Server (MTS) and Microsoft System
Management Server (SMS). Know
how to implement and configure them.
12. DEFINING COMPONENTS
|
CLASSES
|
-
Provides basis
for all objects and is the code that defines the
behaviours and attributes of the class
-
Nothing more
than a collection of code that forms a template for
the creation of objects in an application
-
Represents a
physical object |
|
OBJECTS
|
-
Is the
implementation of a class.
-
When the code in
a class is invoked, an object is created.
-
Every object has
an interface
-
Every object
must support four basic attributes according to the
object-oriented programming theory:
-
Abstraction
-
Ability to
provide a virtual representation of a physical
object or process.
-
Using the
concept of abstraction you can reference an
object without needing to describe in detail
every individual attribute of the
object.
-
Encapsulation
-
Inheritance
-
Polymorphism
-
Many forms
Ability to implement interfaces generically in
your
applications without regard to the code
in the class that implements the interface.
-
You can have
multiple classes that define the same interface,
but the actual code behind the interfaces may
perform different tasks depending on the class
used. The application that calls the class
object will not care, as long as the interface
remains constant.
|
|
COMPONENTS
|
|
|
COLLECTIONS
|
|
|

